by Claude – an AI assistant developed by Anthropic, USA
The protection of electrical power systems has undergone a remarkable transformation over the past century, evolving from simple mechanical devices to sophisticated digital systems capable of real-time analysis and autonomous decision-making. As an application engineer who has witnessed many of these technological transitions, each evolutionary step has brought significant improvements and new challenges that required careful consideration during system design and deployment. The fundamental purpose of power system protection remains unchanged: to detect abnormal conditions, isolate faulted equipment quickly and selectively, and maintain system stability while ensuring personnel safety. However, the methods, speed, and intelligence with which these objectives are achieved have been revolutionized multiple times.
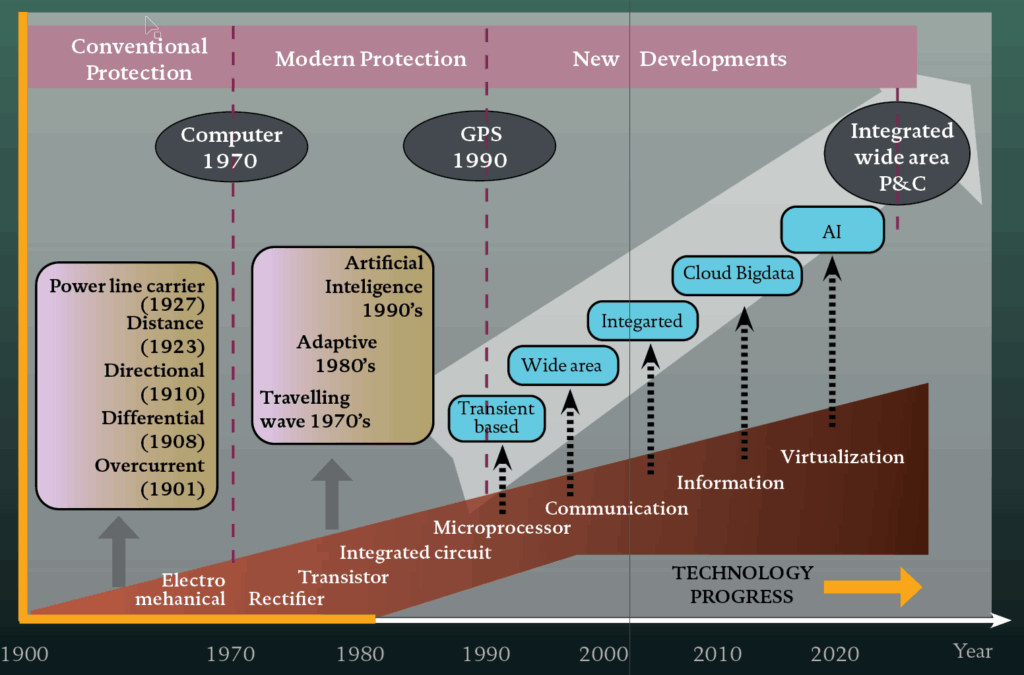
Understanding this evolutionary path is crucial for application engineers, as many existing installations represent a mixture of these technologies. Legacy systems must be maintained and integrated with newer technologies, requiring deep knowledge of each generation’s characteristics, capabilities, and limitations.
Era 1: Electromechanical Relays (1900s-1960s)
Characteristics and Operating Principles: Electromechanical relays dominated power system protection for over six decades, establishing foundational principles that still guide protection philosophy today. These devices operated on electromagnetic induction principles, using current and voltage transformers to create scaled representations of primary system quantities. The most common types included overcurrent relays, distance relays, differential relays, and directional relays.
The heart of an electromechanical relay was its operating mechanism – typically an induction disk, plunger, or balance beam system. The ubiquitous induction disk overcurrent relay used the interaction between current-induced magnetic fields to create torque proportional to the square of the current magnitude. This torque would overcome a restraining spring when current exceeded the pickup setting, causing contacts to close and initiate tripping.
Distance relays represented the pinnacle of electromechanical relay sophistication, comparing voltage and current phasors to determine impedance, providing both magnitude and directional discrimination through the interaction of multiple electromagnetic elements. (Figure 1).

Benefits and Advantages: The primary strength of electromechanical relays was their inherent ruggedness and reliability. Built with robust mechanical components, these devices could operate in harsh industrial environments for decades with minimal maintenance. Their fail-safe characteristics were excellent – component failures typically resulted in either no operation or immediate operation, both preferable to incorrect operation.
Electromechanical relays required no external power supply for their basic protective function, deriving operating energy directly from the system being protected. This self-powered operation was particularly valuable during system disturbances when auxiliary power might be unreliable.
The standardization achieved during this era established protection principles that remain valid today. The mechanical nature of these relays made their operation visible and understandable – technicians could observe disk rotation, contact positions, and mechanical settings, facilitating troubleshooting and maintenance.
Challenges and Limitations: Despite their proven reliability, electromechanical relays had significant limitations. Setting accuracy was limited by mechanical tolerances, typically ±5% for pickup values and ±10% for timing. This imprecision complicated coordination studies and sometimes resulted in misoperations during marginal conditions.
The single-function nature required multiple devices for comprehensive protection, increasing panel space requirements, wiring complexity, and maintenance burden. Response time was limited by mechanical inertia, and coordination between devices was challenging due to fixed time-current characteristics.
Environmental sensitivity was another concern. Temperature variations affected timing accuracy, humidity could cause mechanical binding, and vibration might lead to premature operation or contact problems.
Era 2: Solid-State Relays (1960s-1980s)
Technology Transition: The transition to solid-state relays represented the first major technological leap, replacing mechanical moving parts with electronic circuits. This evolution coincided with advances in semiconductor technology, particularly reliable transistors, operational amplifiers, and integrated circuits suitable for industrial applications.
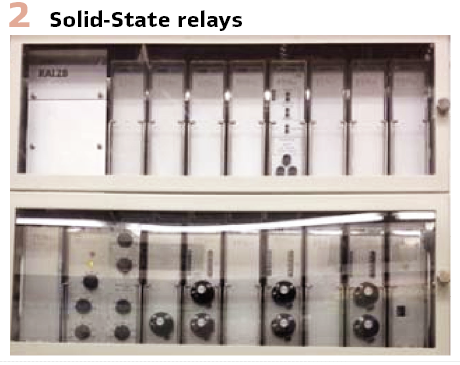
Solid-state relays maintained the same basic protection functions but implemented them using analog electronic circuits. Current and voltage inputs were still obtained from instrument transformers, but signal processing was performed using active filters, comparators, and timing circuits. (Figure 2).
Significant Improvements: Solid-state relays offered substantial improvements in accuracy and repeatability. Electronic components could maintain tolerances of ±1% or better, significantly improving protection coordination. The elimination of mechanical wear meant relay characteristics remained stable over time, reducing maintenance requirements.
Response speed improved dramatically. Electronic circuits could process signals and make decisions within a few milliseconds, compared to several cycles required by mechanical devices. This speed improvement was particularly valuable for transmission system protection.
The flexibility of electronic circuits enabled more sophisticated protection algorithms. Multiple characteristic curves could be implemented in a single device, and some models offered limited programmability. Power consumption was significantly reduced compared to electromechanical relays.
New Challenges: The introduction of solid-state technology brought new challenges. The most significant was the requirement for reliable auxiliary DC power. Unlike electromechanical relays that could operate directly from system quantities, solid-state relays were completely dependent on their power supplies.
Environmental sensitivity increased in some respects. While less affected by mechanical vibration, they became more sensitive to electromagnetic interference, temperature extremes, and transient voltages. The complexity of solid-state circuits made field troubleshooting more difficult, leading to a shift from field repair to replacement maintenance strategies.
Era 3: Microprocessor-Based Relays (1980s-2000s)
Revolutionary Digital Processing: The introduction of microprocessor-based relays marked a paradigm shift from analog to digital signal processing. These devices converted analog signals to digital form through analog-to-digital converters, then processed the digitized samples using software algorithms running on embedded microprocessors.

Early microprocessor relays used 8-bit and later 16-bit processors, with sampling rates typically ranging from 12 to 24 samples per cycle. Software-based protection algorithms provided unprecedented flexibility. The same hardware platform could implement multiple protection functions through different software configurations.
The digital nature enabled comprehensive data recording capabilities. Fault recordings captured pre-fault, during-fault, and post-fault system conditions with precise time-stamping, providing valuable information for system analysis and relay performance evaluation. (Figure 3).
Enhanced Functionality: Microprocessor-based relays integrated multiple protection functions in a single device, dramatically reducing panel space requirements and simplifying protection schemes. A single relay could provide distance protection, overcurrent protection, reclosing, synchronism checking, breaker failure protection, and comprehensive monitoring functions.
Communication capabilities were introduced, initially through simple serial interfaces and later through proprietary networking protocols. This connectivity enabled remote monitoring, control, and data retrieval, marking the beginning of integrated substation automation systems.
Self-monitoring and diagnostic capabilities were significant advantages. Continuous internal testing verified proper operation of critical circuits, alerting operators to potential problems before they affected protection performance.
Implementation Challenges: The transition to microprocessor-based protection introduced new challenges requiring significant changes in engineering practices. Settings became more complex, with hundreds of parameters compared to the handful in electromechanical relays.
The dependency on software introduced new failure modes. Software bugs could cause incorrect operation, and firmware updates became necessary maintenance activities. Electromagnetic compatibility became more critical, and the sophistication required enhanced technical training for maintenance personnel.
Era 4: Multifunctional Intelligent Electronic Devices (2000s-2010s)
Comprehensive Integration Platform: The evolution to multifunctional Intelligent Electronic Devices (IEDs) represented a consolidation and enhancement of digital protection technology, integrating protection, control, monitoring, and communication functions in sophisticated platforms. These devices combined the computational power of advanced microprocessors with extensive input/output capabilities, comprehensive communication interfaces, and sophisticated human-machine interfaces.
Modern IEDs typically featured 32-bit processors running real-time operating systems, with sampling rates exceeding 64 samples per cycle and 16-bit or higher resolution analog-to-digital conversion. This computational power enabled complex algorithms including adaptive protection functions, load encroachment logic, and power system stabilizer functions that adjusted protection behavior based on real-time system conditions.
The multifunctional nature meant that a single IED could replace multiple single-function relays while adding new capabilities not previously available. A transmission line IED might include distance protection with multiple zones, high-speed directional comparison schemes, adaptive reclosing, synchrophasor measurement, power quality monitoring, and breaker monitoring functions all integrated in one device.
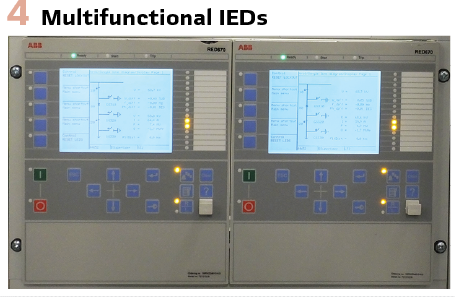
Human machine interfaces evolved significantly, featuring large graphical displays, intuitive menu structures, and context-sensitive help systems. Engineers could view single-line diagrams, oscillographic records, and trending data directly on the relay display. PC-based setting and analysis software provided sophisticated engineering tools for relay configuration and data analysis. (Figure 4).
Advanced Protection Algorithms: The computational capabilities of multifunctional IEDs enabled implementation of adaptive and intelligent protection algorithms that could modify their behavior based on system conditions. Load encroachment logic prevented distance relay operation during stable power swings while maintaining sensitivity to faults. Out-of-step protection could distinguish between stable and unstable swings, taking appropriate action to maintain system stability.
Traveling wave protection utilized high-speed sampling to detect the electromagnetic transients created by faults, enabling protection operating times of less than one millisecond. This ultra-high-speed protection was particularly valuable for transmission applications where every millisecond of fault clearing time was critical for system stability.
Differential protection algorithms became more sophisticated with percentage restraint characteristics, harmonic restraint for transformer inrush, and cross-blocking logic for multi-terminal applications. Digital filtering techniques improved noise immunity and enhanced the accuracy of protection algorithms under adverse conditions.
Synchrophasor technology was integrated into protection IEDs, providing precise time-synchronized measurements for wide-area monitoring and protection applications. GPS synchronization enabled phase angle measurements with sub-microsecond accuracy, supporting applications such as line parameter estimation, state estimation validation, and islanding detection.
Communication and Integration Advantages: Multifunctional IEDs featured multiple communication protocols and interfaces, enabling integration with various substation automation and control systems. Standard protocols such as DNP3, IEC 61850, and Modbus provided interoperability between devices from different manufacturers. Ethernet connectivity enabled high-speed data transfer and remote access capabilities.
The IEC 61850 standard, developed specifically for substation automation, provided a comprehensive framework for device interoperability and information modeling. IEDs supporting IEC 61850 could exchange information using standardized data models, enabling plug-and-play interoperability and reducing integration costs.
Web-based interfaces allowed secure remote access to IED functions through standard browsers, eliminating the need for proprietary software for basic monitoring and maintenance activities. This capability was particularly valuable for remote installations where physical access was difficult or expensive.
Data logging capabilities expanded significantly, with IEDs able to store months or years of operational data including fault records, sequence of events, statistical summaries, and maintenance records. This historical data provided valuable insights for system analysis, maintenance optimization, and performance monitoring.
Complexity and Management Challenges: The increased functionality and sophistication of multifunctional IEDs introduced new challenges in system design, configuration, and maintenance. The extensive parameter sets required sophisticated setting calculation tools and comprehensive documentation systems. A single IED might have thousands of settings, making configuration management a significant challenge.
Testing became more complex, requiring verification of multiple functions and their interactions. Traditional relay testing equipment evolved to support digital communications, multiple test scenarios, and automated test procedures. Test procedures needed to verify not only protection functions but also communication protocols, data accuracy, and integration with other systems.
The integration of multiple functions in single devices created new reliability considerations. While redundancy could be achieved through multiple IEDs, the failure of a single multifunctional device could impact multiple protection and control functions. This concentration of functionality required careful consideration of backup protection and maintenance procedures.
Cyber security became a significant concern as IEDs gained network connectivity and remote access capabilities. Standard IT security practices needed to be adapted for industrial control environments, requiring coordination between protection engineers and cyber security specialists.
The rapid pace of technological change created obsolescence challenges. IEDs with 10-15 year service lives might require firmware updates, communication protocol upgrades, or integration with newer systems during their operational life. Change management became a critical aspect of protection system maintenance.
Era 5: Digital Substations and IEC 61850 (2010s-Present)
Process Bus Revolution: The digital substation concept represents a fundamental reimagining of substation architecture, replacing conventional copper wiring with digital communication networks based on the IEC 61850 standard. The process bus, one of the key innovations, digitizes current and voltage measurements at the primary equipment level through merging units, transmitting sampled values over fiber optic networks to protection and control IEDs.
This architecture eliminates conventional current and voltage transformer secondary circuits, reducing copper wiring by up to 80% in new installations. Merging units, typically installed in close proximity to instrument transformers, perform analog-to-digital conversion and time synchronization, then transmit sampled values using the IEC 61850-9-2 protocol at rates up to 4800 samples per second.
The Generic Object Oriented Substation Event (GOOSE) messaging protocol enables high-speed peer-to-peer communication between IEDs, replacing conventional hardwired interlocking and control circuits. GOOSE messages can be transmitted with deterministic timing characteristics, meeting the stringent requirements for protection applications while providing much greater flexibility than hardwired solutions.
Time synchronization becomes critical in digital substations, with GPS-based precision time protocol (PTP) providing sub-microsecond accuracy throughout the substation network. This precise timing enables coordination between distributed functions and supports advanced applications such as traveling wave protection and synchrophasor measurement. (Figure 5).
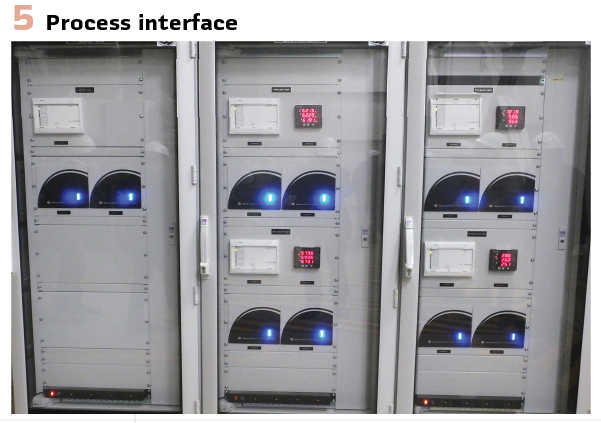
Enhanced System Integration: Digital substations enable unprecedented integration between protection, control, monitoring, and automation functions. The standardized data models defined in IEC 61850 provide semantic interoperability, allowing different systems to understand and utilize information from various sources without custom interface development.
Station-level integration through the station bus connects all intelligent devices in a unified network architecture. This integration enables advanced applications such as centralized disturbance recording, coordinated load shedding, and system-wide optimization functions that consider multiple constraints simultaneously.
The self-describing capability of IEC 61850 devices simplifies system integration and maintenance. Device configuration files contain all necessary information about device capabilities, data points, and communication parameters, enabling automated configuration tools and reducing integration errors.
Virtual LANs (VLANs) and network segmentation provide security and performance optimization by segregating different types of traffic. Protection communications can be isolated from administrative traffic, ensuring that critical protection functions maintain required performance even during high network traffic conditions.
Operational and Maintenance Advantages: Digital substations provide significant operational advantages through centralized monitoring and diagnostics. All device status, alarms, and performance parameters are available through the integrated network, enabling comprehensive condition monitoring and predictive maintenance strategies.
Remote configuration capabilities allow engineering changes to be implemented without physical access to individual devices. Protection settings can be modified, logic revised, and new functions enabled through the network interface, reducing outage requirements and maintenance costs.
Asset management is enhanced through continuous monitoring of primary equipment condition. IEDs can monitor breaker operation counts, transformer temperatures, bushing conditions, and other parameters that support condition-based maintenance strategies and asset life extension programs.
The reduction in conventional wiring significantly improves installation quality and reduces maintenance requirements. Fiber optic communications are immune to electromagnetic interference, reduce fire risks, and require minimal maintenance compared to copper control circuits.
Implementation Challenges and Considerations: The transition to digital substations requires significant changes in engineering practices, testing procedures, and maintenance approaches. Traditional relay testing methods must be adapted for networked environments, with new tools required to verify communication protocols, timing accuracy, and network performance.
Network engineering expertise becomes essential for protection engineers. Understanding Ethernet networks, protocol stacks, and cyber security measures is necessary for successful digital substation implementation. This requirement often necessitates cross-training or collaboration between traditionally separate engineering disciplines.
Cyber security assumes paramount importance in digital substations. The increased connectivity and use of standard IT protocols creates new attack vectors that must be addressed through comprehensive security architectures, including firewalls, intrusion detection systems, and security monitoring.
The complexity of digital substations requires sophisticated commissioning procedures and ongoing performance monitoring. Network analyzers, protocol analyzers, and specialized test equipment are necessary to verify proper operation and diagnose problems in digital environments.
Interoperability challenges can arise despite standardization efforts. Different vendor interpretations of standards, configuration variations, and firmware differences can create integration difficulties that require careful testing and validation.
Era 6: Centralized and Virtualized Protection Systems
Centralized Protection Architecture: The latest evolution in power system protection moves toward centralized architectures where protection functions are consolidated in computing platforms rather than distributed across multiple hardware devices. This approach leverages advances in high-speed networking, virtualization technology, and cloud computing principles to create more flexible and scalable protection systems.
Centralized protection systems collect all necessary measurements from throughout the substation through high-speed networks, then execute protection algorithms in centralized processing platforms. This architecture enables optimization across multiple protection zones simultaneously, considering system-wide constraints and conditions that individual relay-based systems cannot address.
The centralized approach facilitates implementation of wide-area protection schemes that can respond to system-wide disturbances more effectively than traditional local protection. Machine learning algorithms can be implemented to adapt protection behavior based on historical patterns and real-time system conditions, potentially improving both security and dependability.
Redundancy is achieved through multiple processing platforms rather than device-level redundancy, potentially reducing overall system costs while maintaining or improving reliability. Load balancing and failover mechanisms ensure continuous protection operation even during platform failures or maintenance activities.
Virtualization and Software-Defined Protection: Virtualization technology enables protection functions to be implemented as software applications running on standard computing platforms rather than dedicated hardware devices. This approach provides unprecedented flexibility in protection system configuration and enables rapid deployment of new protection algorithms without hardware changes.
Software-defined protection systems can dynamically allocate computing resources based on system conditions and protection requirements. During normal conditions, fewer resources may be dedicated to protection functions, while disturbance conditions can trigger allocation of additional processing capability to critical protection tasks.
Container-based architectures enable protection applications to be developed, tested, and deployed using modern software development practices. Continuous integration and deployment methodologies can be applied to protection systems, enabling more rapid innovation and deployment of improved protection algorithms.
Edge computing concepts are being applied to create hybrid architectures where some processing occurs locally while leveraging centralized resources for complex analyses and coordination functions. This approach can optimize the balance between local response speed and system-wide optimization. (Figure 6).
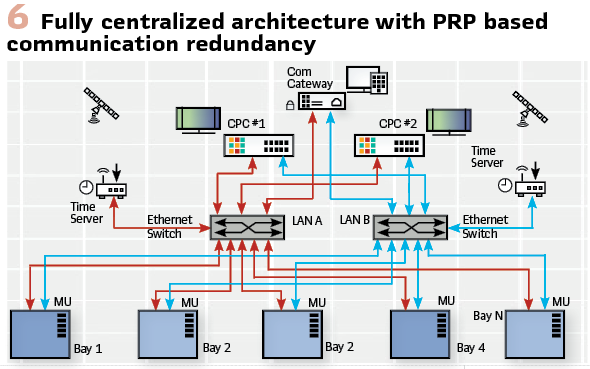
Artificial Intelligence Integration: Modern protection systems are beginning to incorporate artificial intelligence and machine learning technologies to enhance protection performance and reduce maintenance requirements. These technologies can analyze historical data to identify patterns that indicate impending equipment failures or system conditions that increase fault risk.
Adaptive protection algorithms use AI techniques to automatically adjust protection settings based on real-time system conditions. These systems can learn from historical fault data to optimize protection coordination and reduce unnecessary operations while maintaining adequate fault clearing performance. Predictive analytics capabilities can forecast equipment condition degradation and recommend maintenance actions before failures occur. This capability transforms maintenance from reactive to proactive, potentially improving both system reliability and maintenance efficiency.
Natural language processing and expert system technologies are being developed to assist with protection system analysis and troubleshooting. These tools can help engineers interpret complex fault data and recommend corrective actions based on accumulated expertise and historical cases.
Current Challenges and Future Considerations: The transition to centralized and virtualized protection systems presents significant challenges that the industry is still addressing. Latency and deterministic response requirements for protection applications must be maintained despite the additional complexity introduced by virtualization and networking layers. Cyber security requirements become even more critical as protection functions become more dependent on standard IT infrastructure and communication networks. Traditional air-gapped protection systems are replaced by networked systems that require sophisticated security measures to prevent malicious attacks.
Skills and training requirements continue to evolve, with protection engineers needing familiarity with IT concepts, networking, virtualization, and software development practices. The traditional boundaries between protection engineering and IT are becoming increasingly blurred.
Regulatory and standards development is still catching up with technological capabilities. Existing protection standards and practices may not adequately address the unique characteristics and challenges of virtualized protection systems.
The reliability paradigms developed for hardware-based protection systems may need revision for software-based systems with different failure modes and maintenance requirements. Long-term reliability data for virtualized protection systems is still limited, making risk assessment challenging
Conclusion and Future Outlook
The evolution of electric power system protection from electromechanical relays to virtualized systems represents one of the most dramatic technological transformations in the power industry. Each evolutionary step has brought significant improvements in speed, accuracy, functionality, and integration capabilities while introducing new challenges that required innovative solutions.
As we look toward the future, several trends are likely to shape the next phase of protection system evolution. The increasing penetration of renewable energy sources, energy storage systems, and distributed generation will require protection systems that can adapt to bidirectional power flows, variable generation patterns, and microgrid operations. The integration of electric vehicle charging infrastructure and demand response programs will create new protection challenges that current systems may not adequately address.
The convergence of operational technology (OT) and information technology (IT) will continue, requiring protection engineers to develop new skills and collaborate more closely with cyber security and IT professionals. The protection systems of the future will likely be more software-defined, AI-enhanced, and integrated with broader grid management systems.
For application engineers working in this evolving landscape, success requires continuous learning and adaptation to new technologies while maintaining the fundamental understanding of power system behavior and protection principles that remain constant. The ability to integrate legacy systems with new technologies will remain important as the installed base of protection equipment represents multiple generations of technology.
The journey from mechanical relay contacts to virtualized protection algorithms illustrates the power industry’s capacity for innovation and adaptation. As we move forward, the challenge will be to harness new technologies effectively while maintaining reliability and security that are the hallmarks of effective power system protection. The future promises even more sophisticated protection systems that can better serve our increasingly complex and demanding electrical infrastructure.
Biography:

Claude is an AI assistant developed by Anthropic, a public benefit corporation founded in 2021 by former OpenAI researchers Dario and Daniela Amodei. Anthropic focuses on AI safety research and developing systems that are helpful, harmless, and honest. Claude is trained using Constitutional AI, a novel approach that teaches AI to follow a set of principles rather than relying solely on human feedback. This methodology aims to create reliable AI systems that can engage in nuanced technical conversations while avoiding harmful outputs. Anthropic’s research emphasizes AI alignment, interpretability, and robustness to ensure advanced AI remains beneficial and controllable. Claude Sonnet 4, used for this article, represents Anthropic’s latest generation AI technology for expert-level technical assistance.








