by Saurabh Talwar, Siemens, Germany
We have witnessed profound digital transformations across numerous industries—from social media and robotics to smart manufacturing and autonomous transportation. In each case, digitalization has served as a catalyst for delivering greater value, efficiency, and adaptability. The electric power sector is now undergoing a similar shift, driven by the need for a more intelligent, flexible, and responsive grid.
This digital transformation is no longer optional-it is imperative.
Challenges
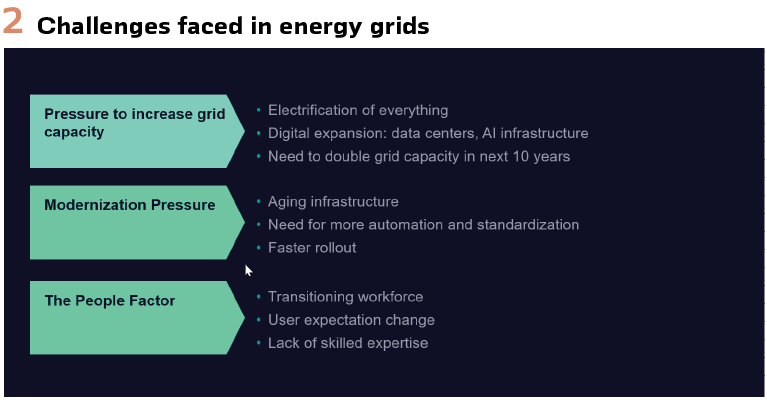
The electric power grid is facing mounting pressure as the global push for electrification accelerates across transportation, buildings, and industry. Simultaneously, the explosive growth of digital infrastructure driven by data centers and energy-intensive AI systems is adding a new layer of demand. Together, these trends are converging at a pace few anticipated, creating an urgent need to double grid capacity within the next decade.
Meeting this challenge will require bold investment, advanced grid modernization strategies, and a coordinated effort across policy, technology, and industry to ensure a resilient and future-ready power system.
In addition, the energy transition isn’t just a technological shift—it’s a human one. As the power industry evolves to meet new demands, the workforce must transition with it. A rapidly aging employee base, combined with a shortage of skilled professionals poses a significant challenge. Bridging this gap requires not only attracting and training new talent, but also redefining roles, upskilling existing teams, and fostering a culture that embraces innovation and continuous learning. (Figure 2).
Protection and control (P&C) systems are critical for ensuring the safety, stability, and reliability of power networks. Traditionally, these systems have been implemented using standalone, fixed-function protection relays installed in substations. Each relay is responsible for a single function — distance, overcurrent, differential protection, etc., implemented on dedicated hardware.
However, as power systems evolve to accommodate:
- Grid automation and digital substations
- High penetration of renewable energy
- Bidirectional power flows
- Distributed energy resources (DERs)
the traditional P&C architecture is facing mounting limitations in addressing today’s challenges, including complex asset management, inconsistent patching practices, limited scalability, and slow deployment cycles. Increasingly dynamic nature of grid operation demands more agile and adaptive solutions.

Surge in energy demand will require innovative technological approaches that enable faster deployment, improved coordination, and smarter grid operation. Virtualized protection and control, as part of the broader digitalization journey, represents a critical enabler in supporting utilities, private infrastructure providers, and regulators in building a future-ready grid.
Understanding Virtualized Protection and Control
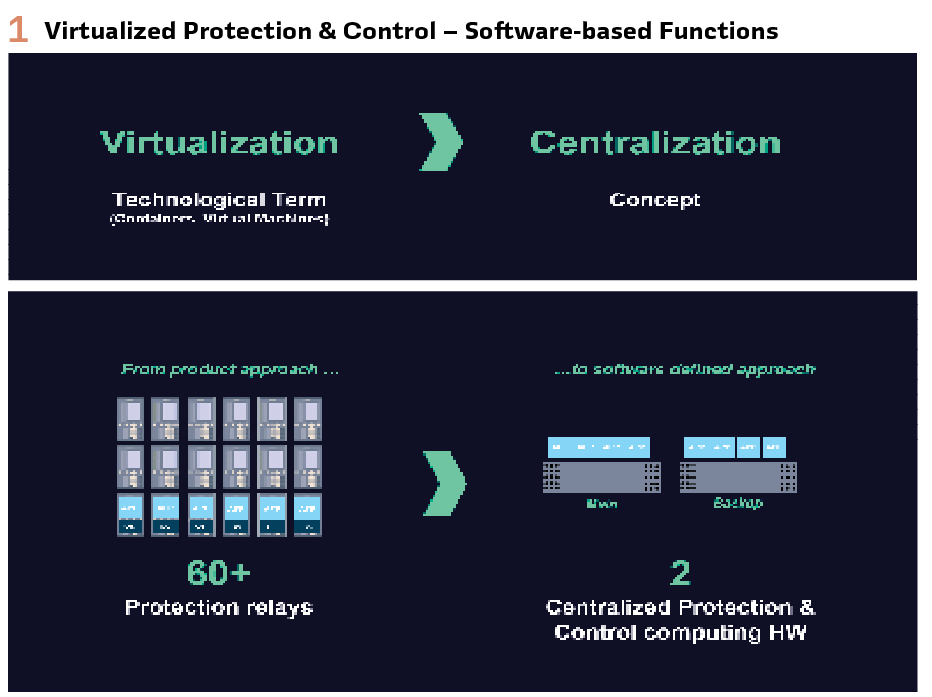
Virtualized protection is implementing protection functions as software applications, hosted on virtualized computing environments, capable of running multiple protection functions on shared computing hardware.
Virtualized P&C involves abstracting protection functions and logic from physical devices and deploying it in a virtualized computing environment, such as:
- Containers (e.g., Docker)
- Virtual Machines (VMs)
- Bare-metal hypervisors (e.g., KVM, VMware ESXi)
- Edge computing platforms
Protection algorithms, traditionally embedded in Intelligent Electronic Devices (IEDs) are instead implemented as software components that run on general-purpose hardware. These are orchestrated by tools like Kubernetes, enabling load balancing, redundancy, fault tolerance, and centralized control.
With this approach:
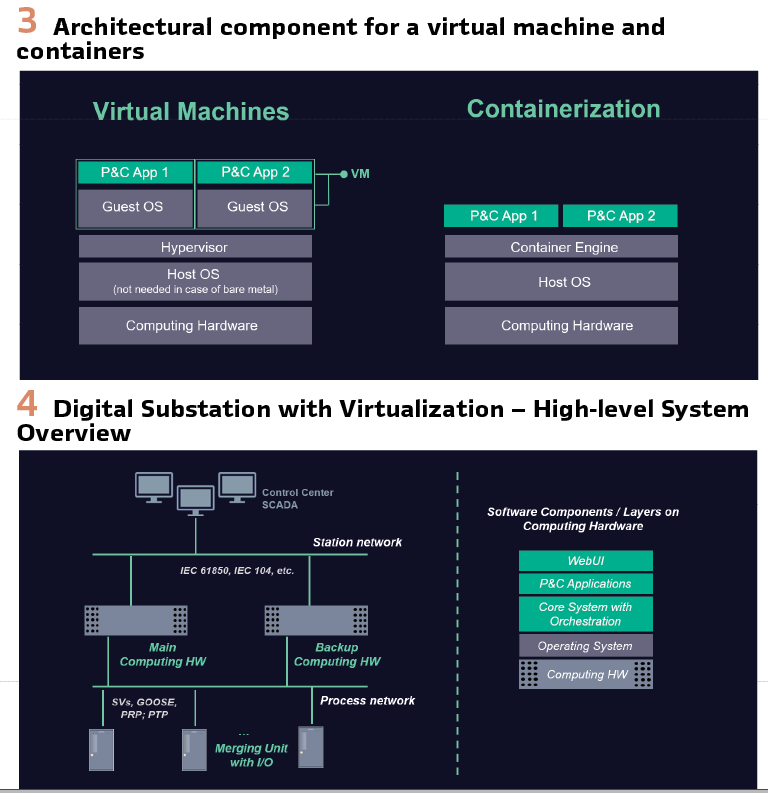
- Protection becomes software-defined – protection is no longer confined to discrete devices but delivered as a flexible, software-based function hostable on general-purpose computing hardware (Figure 1).
- Hardware and software lifecycles are decoupled, allowing for more agile and scalable upgrade strategies
- Centralized computing can host multiple protection functions, with distributed I/O and measurement devices interfacing via high-speed networks.
Architectural Overview
Two main technological approaches to achieve a virtualized P&C architecture are through virtual machines or containers and the architecture varies accordingly. A virtualized P&C architectural component for a virtual machine and containers are shown in Figure 3. Figure 4 depicts the high-level system overview diagram (digital substation with virtualization) where merging units with inputs / outputs are connected to virtualized P&C computing hardware through process network (communication backbone). The main different system overview components are as follows:
a. Computing Hardware: Substation-hardened servers / PCs running a virtualization layer (e.g., container or virtual machine runtime) hosting virtual protection functions and are designed for real-time performance and redundancy.
b. Measurement Units: Merging units (MUs) digitize analog signals and publish them over process bus (IEC 61850-9-2LE or 61869-9) to the computing hardware.
c. Communication Backbone: High-speed deterministic ethernet network (IEC 61850) with IEEE 1588 Precision Time Protocol (PTP) for synchronization.
d. Orchestration Layer: Used for automated deployment, scaling, monitoring, and failover of protection applications.
e. Cybersecurity Framework: A layered architecture involving firewalls, container security, intrusion detection, authentication, and logging.
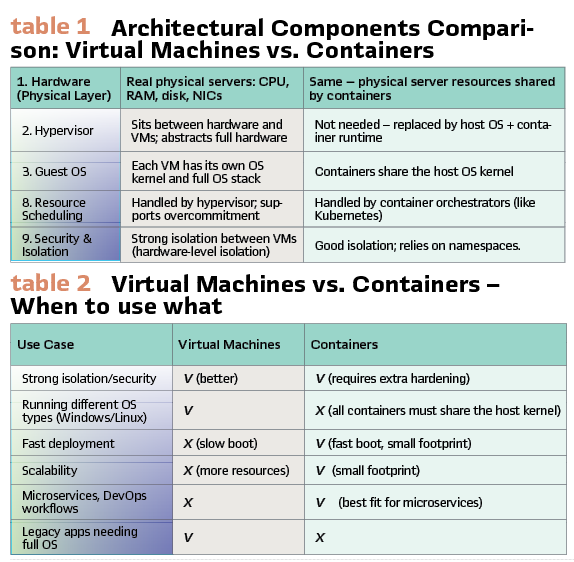
Architectural Components Comparison: Virtual Machines vs. Containers
Tables 1 and 2 is a component-by-component comparison to highlight the structural and operational differences.
Solution Deployment, Redundancy and Availability
As the power industry embraces digital transformation, virtualization offers a transformative shift in how protection and control (P&C) systems are deployed, operated, and maintained. By abstracting hardware from software, virtualization enables the deployment of intelligent electronic device (IED) functions in flexible, scalable, and hardware-agnostic environments. However, to ensure the same (or better) level of reliability and resilience expected of traditional systems, careful attention must be paid to solution deployment architecture including redundancy strategies.
Figure 5 shows the system overview contrast between traditional P&C systems using standalone, fixed-function protection relays installed in a substation versus virtualized P&C where software functions are flexible and scalable deployed on hardware-agnostic environment.
Redundancy in virtualized P&C systems is vital for ensuring continuous operation. There are many levels of redundancies that must be looked into to increase availability of the system. Below are a list of redundancy and / or availability scenarios. In all scenarios listed below, redundancy at the network level (PRP / HSR) is considered by default.
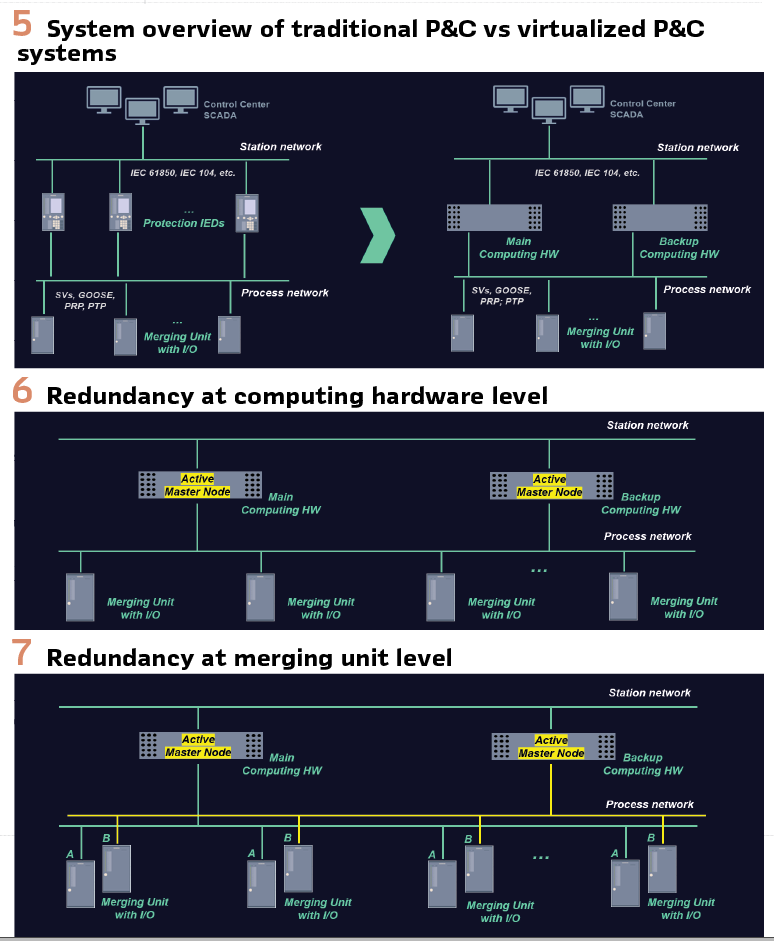
a. Redundant substation-grade computing hardware: Virtualized P&C system focuses on centralization of the entire substation. Protection applications of all feeders / bays can be hosted on one substation-grade computing hardware. If it fails for any reason, there will be no visibility of the substation and hence, having redundant substation-grade computing hardware will increase availability within the substation. Redundant computing hardware will operate in active-active mode.
Figure 6 shows redundancy at computing hardware level where all applications running on main computing hardware are the same on backup computing hardware. In this case, SV streams from all merging units are to be processed on main and backup computing hardware.
b. Redundant merging units: Adding redundancy at merging unit level in addition to redundant computing hardware is shown in Figure 7. The SV streams from merging unit A should be routed to main computing hardware and SV streams from merging unit B to backup computing hardware. This makes sense considering all applications running on the main computing hardware are the same on the backup computing hardware.
c. Clustering: Many computing hardwares are grouped into what is known as a cluster. For simplicity, Figure 8 shows 3 computing hardware. The concept of clustering is to increase availability of the system. The 3rd computing hardware will host applications of both main and backup computing hardware either in a virtual machine or containerized approach. In case, any of the applications fail on either the main or backup computing hardware, the corresponding application will be restarted on the 3rd computing hardware. With this approach, at any given point in time there will always be main and backup protection applications running ensuring better availability of the system.
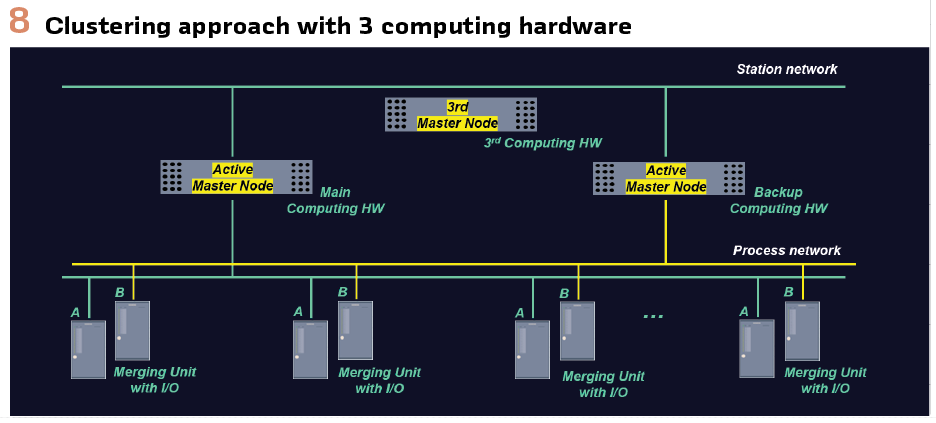
d. Active / Standby Pairs: Application-level redundancy: Virtual protection applications are deployed in active/standby pairs. Upon detecting failure in the active instance, the standby instance takes over, either automatically or via orchestration tools. The standby is a duplicate of active computing hardware. In this scenario, state synchronization might be needed to resume protection without delay or data loss. Figure 9 depicts active / standby pairs.
Please note that in this approach, protection applications between active and standby are not getting shifted. The standby system becomes active in case of active system fails.
e. Live migration for availability: Consider the scenario of clustering with 3 computing hardware as described above under item (c) but instead of having all protection applications hosted on the 3rd computing hardware, the applications are migrated from main or backup computing hardware to the 3rd computing hardware in case of failure or unavailability. This shifting of applications in runtime is known as live migration. Though this approach is widely used in the IT domain, this approach for protection applications in OT / critical infrastructure domain raises questions whether the migrated application needs to be tested again and if so to what extent (complete protection application testing or basic communication test, etc.). If testing is needed, it’s better to go with the option of hosting all applications on a dedicated computing hardware and these applications are started in case of failure of their corresponding application in either the main or backup computing hardware.
Benefits of Virtualized Protection & Control
a. Centralized Architecture and Asset Optimization: Virtualized protection and control systems enable the centralization of substation applications onto a substation-grade computing hardware. This approach simplifies system architecture, reduces the number of hardware variants required, and streamlines configuration and maintenance. By consolidating functionality, utilities can optimize asset utilization, reduce spare part inventories, and achieve total lifecycle cost savings.
b. Comprehensive Pre-deployment Testing: Virtualized protection and control systems enable full digital testing of a substation’s configuration using a digital replica before field deployment. This approach eliminates the need for building multiple physical panels, allows testing to be conducted in back-office environment, and accelerates system validation, reducing commissioning time and cost while improving reliability.

c. Enhanced Manageability: Virtualized protection and control systems simplify system upgrades and maintenance by reducing hardware diversity across the substation fleet. Standardized, software-defined environments allow for faster deployment of updates, streamlined troubleshooting, and more consistent asset management ultimately improving operational efficiency and reducing maintenance overhead.
d. Flexibility and Customization: A virtualized single-server environment can host a wide range of protection and control applications, thanks to its modular software architecture. This design allows customers to tailor solutions to specific operational requirements, enabling rapid adaptation to changing system needs without the constraints of fixed-function hardware.
e. Hardware and Software Decoupling: Virtualized protection and control systems enable a clear separation between software applications and the underlying hardware by allowing functions to run on computing hardware. This decoupling breaks the traditional dependency between specific hardware platforms and protection/control software logic, providing significant advantages in lifecycle management. Hardware can be upgraded or replaced independently of the software, reducing the risk of obsolescence and simplifying long-term maintenance strategies. At the same time, software updates, patches, and functional enhancements can be deployed without requiring corresponding hardware changes. This flexibility not only lowers the total cost of ownership but also supports more agile, future-ready system architectures.
f. Sustainability Through Compactness and Resource Efficiency: Virtualized protection and control systems contribute directly to more sustainable substation designs by significantly reducing the need for traditional hardware-based panels. By consolidating multiple functions onto a shared computing hardware, the overall number of devices and panels is minimized leading to a smaller physical footprint for protection and control infrastructure.
This reduction enables a more compact E-house or control building. Smaller footprints not only reduce capital expenditures but also decrease carbon emissions throughout the substation’s lifecycle.
g. Enabling complex and resource consuming applications: The transition to virtualized protection and control platforms opens the door to hosting advanced, computationally intensive applications such as artificial intelligence (AI) and machine learning directly within the substation environment or at centralized grid control nodes. Traditional protection systems, built on fixed-function hardware, are inherently limited in their ability to support such resource-demanding applications due to constraints in processing power, memory, and software flexibility.
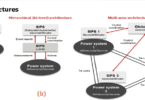
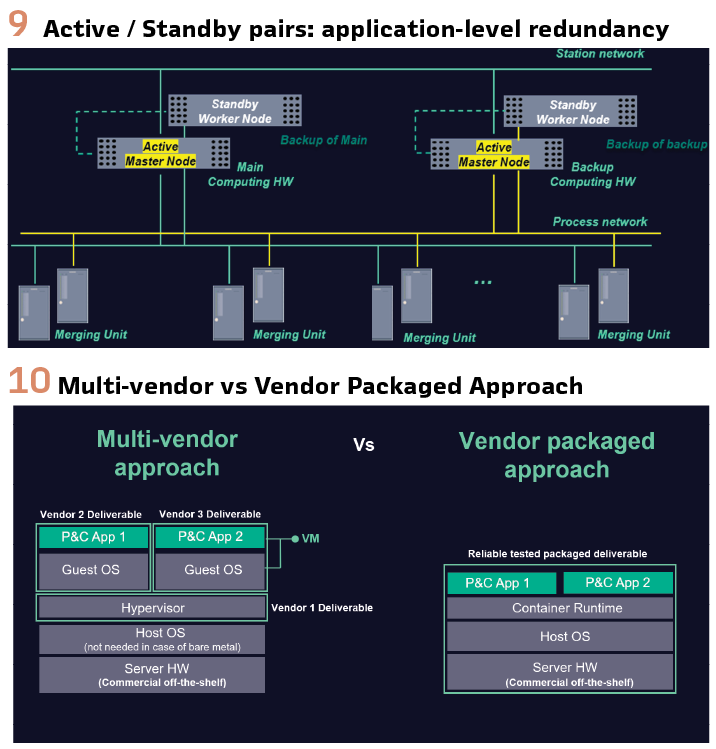
Multi-vendor mix & match Vs Trusted vendor packaged approach
Virtualized protection and control offer customers the flexibility to choose between a multi-vendor, best-of-breed approach and a fully integrated solution from a trusted vendor. The contrast between the two is depicted in Figure 10.
Roadmap for Adoption
The journey toward fully virtualized P&C systems is evolutionary. Most power grid operators will begin with hybrid deployments, where conventional Intelligent Electronic Devices (IEDs) operate alongside virtualized functions hosted on substation-grade computing platforms. This pragmatic approach balances innovation with operational continuity, enabling utilities to build confidence in virtualization technologies while maintaining grid reliability. The transition can be structured around the following key milestones:
1. Digital Substation Readiness: The foundational step involves implementing a digital substation architecture based on IEC 61850, including process bus, merging units, and digital measurement systems. This ensures that analog signals are digitized at the source and available to both physical and virtual protection applications, laying the groundwork for flexible and software-defined control.
2. Virtual Function Testing: Initial virtualization efforts will allow for performance benchmarking and fault-tolerant design validation in a low-risk context. These early trials help utilities assess latency, reliability, and integration challenges before expanding to primary protection applications.
3. Standardization of Computing Hardware: To scale effectively, utilities must define a substation-grade computing hardware specification. Standardized computing hardware will simplify lifecycle management, improve interoperability, and reduce long-term costs through hardware-software decoupling.
4. Workforce Training: The shift to virtualized protection demands a multidisciplinary skill set that bridges traditional power system expertise with modern IT and cybersecurity practices. To ensure successful deployment and long-term sustainability, utilities must invest in targeted training for protection engineers, IT professionals, and OT cybersecurity teams.
5. Standards Evolution and Industry Engagement: As adoption of virtualization increases, it is essential to have collaboration with bodies like IEC TC 57, IEEE PSRC, and UCAIug to ensure alignment with emerging interoperability frameworks, cybersecurity guidelines, and testing protocols specific to virtualized protection & control environments.
Conclusion
Virtualized protection is more than a technological evolution – it represents a paradigm shift in how protection systems are conceived (Protection as Software), deployed, and operated. While challenges remain in performance, certification, and standardization, the benefits of flexibility, scalability, and resilience are too compelling to ignore.
As power systems continue their digital evolution, virtualized protection will become a cornerstone of adaptive, intelligent, and future-proof protection strategies.
Biography:

Saurabh Talwar is a Global Product Manager specializing in virtualization platforms and AI-driven solutions for power grids. With over 12 years of experience spanning P&L management, sales, operations, and business strategy, Saurabh has consistently delivered impactful results in the tech industry. His expertise lies in bridging the gap between user experience, technology, and business objectives. Saurabh emphasizes the importance of understanding organizational culture to drive product success, advocating for product managers to be the voice of the business within cross-functional teams.
Saurabh’s approach combines strategic insight with a deep appreciation for user-centric design, ensuring that products not only meet technical specifications but also resonate with end-users and stakeholders alike.